Ethical Hacking Individual Coursework Assessment | NUS
| University | National University of Singapore (NUS) |
| Subject | Ethical Hacking |
Ethical Hacking ICA
Introduction
This ICA requires the execution of an ethical penetration test against the designated system and the submission of a written report documenting the methodology, findings, and recommendations.
Struggling with Ethical Hacking ICA at NUS?
Scenario
You have been approached by a non-profit environmental organisation seeking a comprehensive security assessment of its IT infrastructure. The organisation frequently handles sensitive information from whistle-blowers and leads major environmental campaigns. The organisation has observed unusual and suspicious activity within its network and systems, raising concerns about potential security vulnerabilities. While the exact weaknesses are unknown, there is a strong suspicion that the systems may be at risk. Your task is to carry out a thorough security test, identify vulnerabilities, and provide detailed recommendations to strengthen the organisation’s overall security posture. For your security analysis, they have provided you with the following network diagram and details:
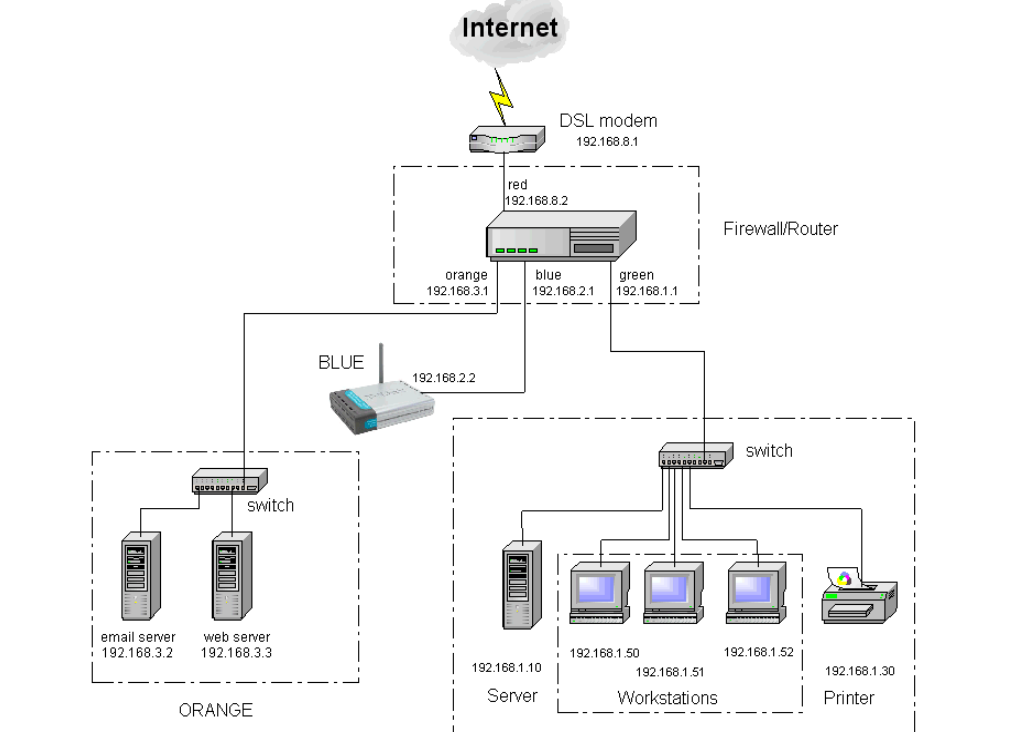
A Linux-based firewall/router controls access to the different zones of the system. Zones are separate network entities, with no traffic permitted between them unless explicitly authorised:
Red — the Internet
Green — the safe zone for maximum protection
. Orange — a DMZ designed for Web, mail, or other Internet servers.
Blue — for wireless networks.
Orange Zone:
The webserver is an Ubuntu 24.04 LTS machine running Apache 2.4.x The email server is a MS Windows Server 2022 Standard, running MailEnable Standard Edition 10.53
Green Zone:
The Server: Windows Server 2022, with Active Directory, DHCP, DNS, IIS.
The server also runs a MySQL Server 8.4.6, the back end for a custom web application that is used by the admin and financial office.
The server contains also shared folders, which are used for different purposes: projects, advisors reports, and other classified and non-classified documents.
The workstations are Windows 11 24H2 machines.
Blue Zone:
Employees and volunteers are allowed to bring their own device and connect to the Internet.
No further details or credentials are provided. The only information available is the public IP address and the domain name of the web server. (As this scenario is hypothetical, placeholders and will be used in the report).
Client Requirements
The client has specifically requested the following conditions for the penetration test:
Data integrity: No data should be lost from any system during the testing. If a change is required for proof-of-concept purposes, you must also identify a procedure to restore the system to its previous state, provided you have first confirmed with the client that a backup exists and is securely stored.
Service continuity: The risk of disrupting services during office hours should be minimised.
Time constraints: As only a limited number of hours are available for this engagement, planning should prioritise the most critical services and components.
Use of tools: Penetration testing activities should be performed using free and open-source software (FOSS) wherever possible. If no suitable option exists for a particular task, you must clearly state the licence terms and associated costs of any proprietary tools proposed.
Task
You should write a report (approximately 4500 words, submitted in PDF format) detailing your plan, with a justification for tools and techniques used, the results and a complete chronological audit trail of hacking actions undertaken, in accordance with applicable professional and ethical standards.
For the practical part, you must carry out a pen testing limited to a given virtual machine (information about location of the virtual machine is available on Blackboard, under “Assessment”). For the rest of the work, use the information provided in the scenario, and make the appropriate and reasonable assumptions if necessary (provide a rationale for it).
The report will have to cover all the stages of the ethical hacking methodology. The report should include at least the following elements (xx% indicates the weight in the mark allocation):
- Demonstration of understanding of the scenario and discussion of the pre-engagement interactions. (10%)
- Identification of relevant tools for each stage of the ethical hacking.(10%)
- Appropriate information gathering and threat modelling (10%)
- Identification of security vulnerabilities (10%)
- Exploitation of the vulnerabilities (10%)
- Post exploitation activities (10%)
- Reporting of the findings and potential suggestions for countermeasures (10%)
- Critical reflection of self-performance and the development of skills for employment as a computer security professional. (10%)
The remaining 20% of the final grade will be awarded based on the overall quality of the report, including formatting, completeness, readability, and appropriate referencing.
Elements 4, 5, 6, and 7 relate to the practical component. You must report your analysis of the assigned virtual machine, and the results of these activities should be documented and explained, with appropriate screenshots included.
For Element 7, you should also provide countermeasures and recommendations derived from the scenario. These must be clearly distinguished from those based on the practical component.
Looking for reliable Ethical Hacking coursework support at NUS?
- SM9532 Strategic Frameworks and Cultural Contexts in International Management Assessment Brief 2026 | NU
- SC1007 Data Structures & Algorithms Assignment Question 2026 | NTU
- SOC309 Contemporary Social Theory Assignment Question 2026 | SUSS
- MKTG2060 International Marketing Assessment 1 Guidelines 2026 | UON
- GPS2301 Interventions & Strategies in Special Needs Education Assignment 2026 | TP
- PSB7022CL Marketing in a Global Age Assignment 2, 2026 | Coventry University
- PSB5045EE Analog and Digital Electronics (ADE) Assignment Questions 2026
- LG71011 Cold Chain Logistics Assessment Project 2026 | ITE College
- BUSM2578 Integrated Perspective on Business Problems Assignment 1 2026 | RMIT
- GSS502 Global Security, Strategy and Leadership Tutor-Marked Assignment – 01, 2026 | SUSS


